
Exceptionally Secured for IT Security Act 2.0
The Future of Cybersecurity for
Your Critical Infrastructure Company
Your Critical Infrastructure Company
How can CI-companies meet the requirements of the IT Security Act 2.0?
Even with the official BSI orientation guide, this question is not easy to answer. What does the "audit according to § 8a BSIG" entail? Are your existing virus scanners and log management systems sufficient? And how can you effectively improve your network without disrupting operations?
You will find answers and solutions to all these questions and challenges!
OMICRON's proven approach to cybersecurity for the power industry
What are OMICRON's advantages?
OMICRON is your partner for cybersecurity solutions in the power grid.
We have been a reliable partner to utilities and grid operators for more than 30 years and have extensive, long-term experience in the industry. The StationGuard and GridOps solutions are 100% developed and manufactured in Germany and Austria. A dedicated team of more than 1000 employees at 24 locations supports our customers in more than 171 countries. Our multilingual technical support is available 24 hours a day, 7 days a week.
What else do I need to be compliant with the IT Security Act 2.0 if I have the StationGuard solution?
The use of StationGuard and GridOps fully meets the requirements for the use of attack detection systems according to the BSI guideline (version 1.0) as well as the legal requirements for an IDS according to § 8a BSIG and § 11 EnWG. This provides you with a solution for the detection of attacks and vulnerabilities (vulnerability management) and the logging of security-relevant events.
StationGuard and GridOps also support the response processes. OMICRON's integrated plant knowledge enables our systems to display clearly understandable event and alarm messages. Network diagrams and unambiguous names based on the plant documentation enable all IT and OT staff to quickly find their way around.
In addition to technical measures, the plant operator must also implement organizational or process-related measures. These include, for example, planning and implementing logging, as well as introducing processes for response and troubleshooting.
How does OMICRON ensure that the IDS does not impact the availability of my assets?
StationGuard is a passive IDS that does not interact with your equipment. The connection via mirror ports (also known as SPAN ports) ensures that the IDS cannot send any packets into the network.
Does StationGuard require a setup period/learning period?
OMICRON has developed a novel Allowlist approach based on its many years of expertise in the field of power analysis. In contrast to conventional signature- or learning-based IDS approaches, this approach enables our StationGuard IDS to be used immediately without a learning period and with improved detection of security-relevant events and faults. The typical commissioning time for StationGuard is 1-3 hours per plant network. After this time, StationGuard is fully parameterized and ready for use without any additional training time.
Stadtwerke Kempen are fully protected
You don't have to be a CI-company to modernize your substation. With our help, Stadtwerke Kempen has secured it for future developments. Take a look:
Interested?
Contact our cybersecurity experts today!

With us, you meet all
information security objectives
Availability | Authenticity | Integrity | Confidentiality
Advanced attack detection for effective vulnerability management
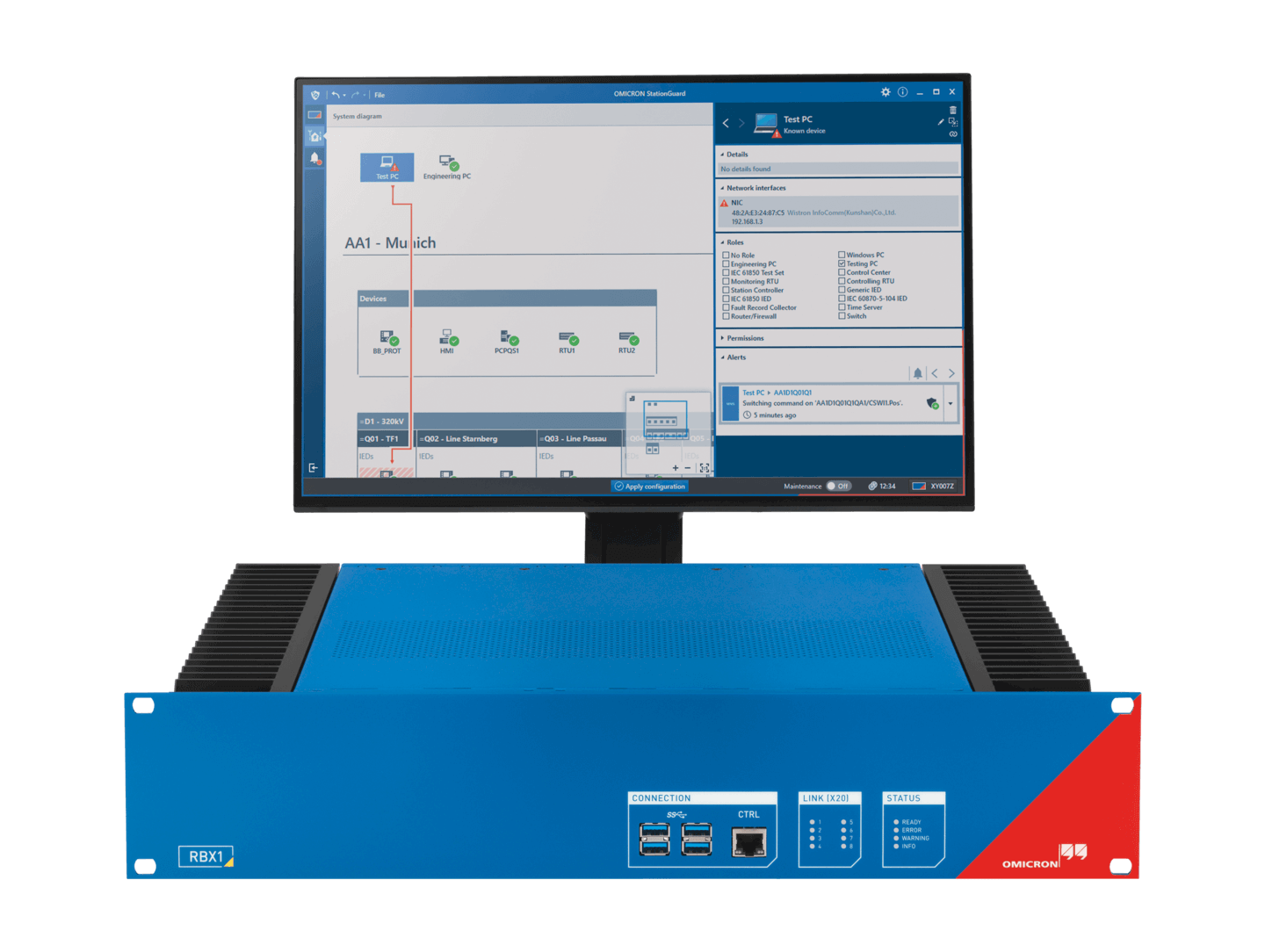
The IDS StationGuard collects detailed data
about each resource. The innovative Allowlist approach
allows for timely and accurate detection of attacks,
reduces false alarms and ensures operational readiness.
All alerts are understood by both OT and IT staff.
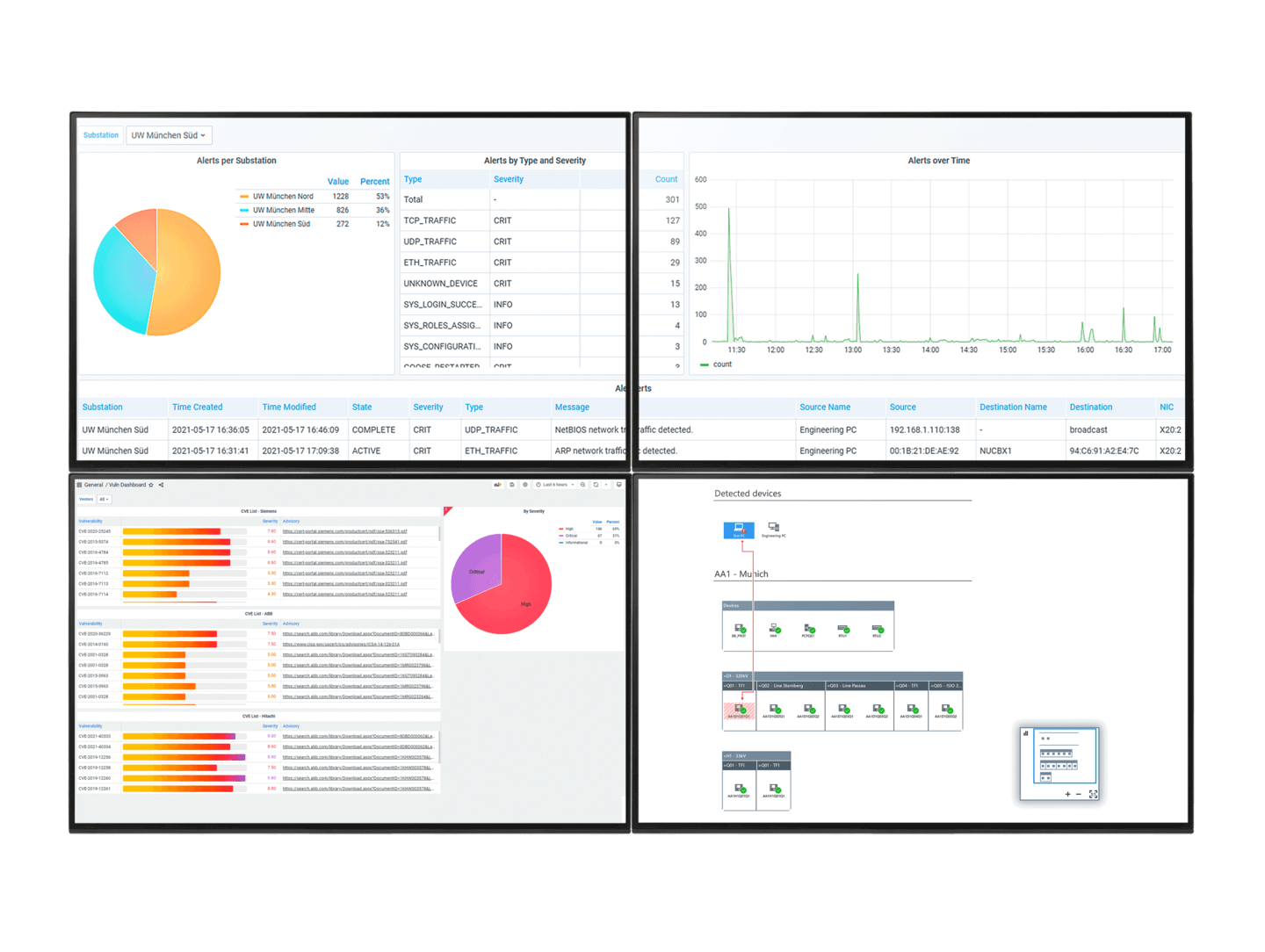
GridOps provides a comprehensive asset inventory,
alert dashboard, sensor management
centralized user management, and
vulnerability management with comprehensive
reporting. See only the relevant vulnerabilities
for successful vulnerability management.
Our Experts for you
These customers rely on OMICRON as well
Documents
Find the answers to all your security questions
About OMICRON electronics
Who can help me with implementation and planning?
OMICRON has many years of experience with IT infrastructure in substations, power plants and control centers. We also have numerous experts who specialize in cybersecurity in the power grid, as well as experts for BSI IT-Grundschutz and ISO 27001 in power utilities. This team will be happy to advise you. For special topics, we can draw on our partner network of consulting companies to provide joint support.
How can I get assistance or support from OMICRON?
The StationGuard user interface provides access to comprehensive StationGuard help with detailed descriptions for each alert type. Our technical support is available to all our customers 24 hours a day, 365 days a year. In addition, we offer expert support for OT device and network vulnerability assessments, as well as our expert 9am–5pm incident management support from our OT security specialists.
How does OMICRON ensure secure development and production of StationGuard and GridOps (keyword: supply chain attacks)?
At OMICRON, we set the highest standards for the development and production of our cybersecurity solutions. Programming and development take place exclusively in the DACH region (Austria and Germany).
Correspondingly high security measures are taken at hardware, software, and process level to harden the development process, the production process and the products themselves against cyber threats. StationGuard and GridOps are developed according to an audited Secure Software Development Life Cycle (SSDLC). See also our separately available [whitepaper] on this topic.
About the IT Security Act 2.0
How exactly does vulnerability management or the vulnerability database help me?
GridOps has a vulnerability database that monitors all your assets or resources live for vulnerabilities. This database contains all security advisories published by device vendors for each asset. GridOps has a built-in device database that can identify sub-components, plug-in cards, and their firmware versions to provide the most accurate vulnerability management for protection and control devices.
With our built-in vulnerability management, GridOps shows you
- which of your protection and automation devices are affected by a disclosed vulnerability (CVE or Security Advisory),
- automatically assesses their criticality based on CVSS, and
- shows you remediation options, such as a firmware update or configuration advisories.
What is “DPI” and which protocols are supported?
For IT and OT protocols, our attack detection system includes advanced and effective anomaly detection based on our integrated Deep Packet Inspection (DPI) to protect against cyber-attacks at an early stage. We perform a detailed analysis of transmitted data packets and their content on the network.
Supported OT protocols include IEC 61850 MMS, GOOSE, IEC 62439-3 PRP and HSR (with RedBox), IEC 60870-5-104; DNP3; Modbus TCP; IEC 62056 (DLMS/COSEM); IEEE C37.118 (Synchrophasor); IEEE 1703-2012 / ANSI C12.22 (AMI Protocol); IEC 60870-6 (ICCP/TASE.2 - UCA 2.0); SIEMENS S7; EtherCAT; Profinet; etc.
Supported IT protocols include FTP; HTTP; HTTPS (without decryption, but with application detection); RDP; NTP; NetBIOS (Windows File Sharing); ARP; DHCP; MySQL; MSSQL; PostgreSQL; SSH (without decryption, but with application detection); Telnet; ICMP / ICMPv6; RIPv2; SSDP; MDNS; etc.
What is “Functional Monitoring?”
An additional feature of our StationGuard intrusion detection system is the integrated functional monitoring of the plant network. This allows you to monitor not only cybersecurity parameters, but also the proper operation of your automation systems and networks to detect deviations from the target state of the plant. This can include interoperability problems between devices, configuration errors, exceeded transmission times and failed time synchronization.
About StationGuard and GridOps features
Does the StationGuard solution provide real-time alerts and notifications? Can it automatically respond to detected threats?
All events and alerts detected by StationGuard are immediately reported in the StationGuard and GridOps user interfaces, logged on the sensors along with forensic evidence, and routed. In addition, your staff can be separately notified of events and alerts via email according to your reporting and escalation paths.
Because StationGuard is a passive IDS, it does not actively interfere with network traffic or execute commands/switches. In addition, it is possible to implement automated processes that execute pre-programmed automatic responses (e.g., via a SIEM system). This would allow a SIEM or SOAR system to automatically activate firewall rules to block the IP addresses in question after a StationGuard alert, for example.
Can I integrate the IDS StationGuard with my ActiveDirectory or LDAP system?
Yes, LDAP/Active Directory integration can be managed and configured through the GridOps central management system.
How are users and permissions managed? Can I manage roles and permissions myself?
To ensure secure access to your StationGuard instances, you can define different roles and access rights via our central management system GridOps. For example, you can specify that only authorized personnel can make configuration changes or enter maintenance mode. With Role-Based Access Control (RBAC), threats can be reduced and even eliminated.
About the integration of OMICRON's solution
How easy is it to configure and manage the StationGuard solution? How much IT expertise is required?
StationGuard has been designed from the ground up to allow plant operators to operate and configure the intrusion detection system. The training required can be estimated to be as little as one day. StationGuard's built-in knowledge of the system gives it the advantage of requiring little system or IT knowledge from the operators themselves. However, our experts are always available on site or by phone for planning and configuration.
How does OMICRON support me with the integration, installation, and configuration of the IDS?
To ensure a smooth and optimal start of the StationGuard IDS, we support you with our best practice approach. To this end, we first discuss your deployment and application requirements, as well as the structural design of your operator's plant. Our staff will then perform the user-specific pre-configuration of your StationGuard. Installation and integration are carried out by our expert staff at your site.
If desired, we can work with your staff to perform a security assessment of your OT networks and systems.
How does an IDS solution integrate with other security tools and systems in my organization's security infrastructure?
StationGuard and GridOps can easily connect to SIEM and ticketing systems (such as Splunk, FortiSIEM or ServiceNow) via built-in plug-ins. Our easy-to-understand alerts can also be forwarded via the Syslog protocol.
Asset data, e.g., from OMICRON ADMO or ERP systems, can be imported into StationGuard to complete the asset information. By exporting the asset or working capital list from StationGuard to ticket systems, you can easily update, reconcile, and document your asset inventory.
Integration with ticketing systems allows you to automatically create tickets to handle IDS alerts. Tickets can also be automatically assigned to the employee(s) responsible for the asset or location through an imported asset directory.
How can I protect myself from attacks during commissioning, testing, and maintenance?
To protect against cyber-attacks during testing or maintenance of your equipment, we support you with a specially developed "maintenance mode". This can be quickly and easily enabled or disabled via StationGuard. To ensure that no false alarms are triggered even when authorized tasks are being performed, the engineering PCs and test equipment used can be registered in advance in StationGuard. This method can also be used to monitor the activities of service providers during commissioning. This flexible approach allows StationGuard to monitor assets prior to factory acceptance.
Are you interested or do you have further questions?
Please contact our cybersecurity experts!
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.












